What is SSO?
Imagine you’re visiting an amusement park that has many rides and attractions. Normally, you would have to stand in a separate line and get a ticket or pass for each ride or attraction you want to enjoy. This would take up a lot of time and would be frustrating if you needed to go back and forth between attractions.
Now imagine that instead of getting a separate ticket or pass for each ride, you get one pass that grants you access to all the rides and attractions you’re authorized to enjoy. With this one pass, you can move freely between rides and attractions without having to go through the process of getting a new ticket or pass each time.
In this metaphor, the pass is like a set of login credentials, and each ride or attraction is like a different application or service that you need to access. SSO simplifies the process by providing one set of credentials that grants you access to all the applications or services you’re authorized to use, just like the one pass that grants you access to all the rides and attractions you’re authorized to enjoy.

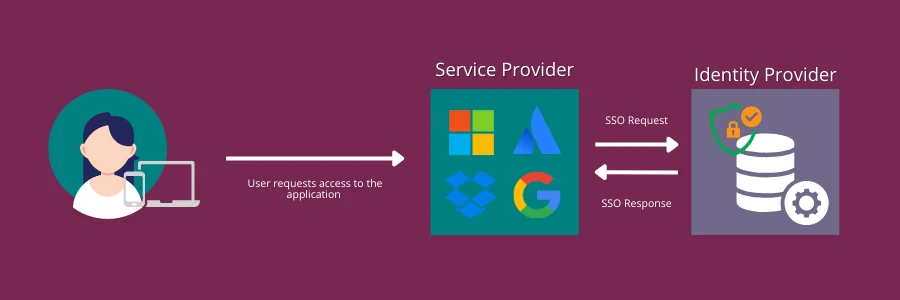
SSO stands for Single Sign-On. It is an authentication mechanism that allows users to access multiple applications or services with a single set of credentials, such as a username and password. Instead of having to log in separately to each application, a user can authenticate once and be granted access to all authorized applications without having to provide their credentials again.
SSO is commonly used in large organizations where employees need to access multiple applications, such as email, document management systems, HR software, and other business applications. It can simplify the login process, increase security, and improve user productivity by reducing the number of times they need to enter their login credentials.
There are different SSO protocols and standards available, including SAML (Security Assertion Markup Language), OAuth, and OpenID Connect. These protocols enable secure communication between applications and identity providers, allowing users to authenticate with a central identity provider and access authorized applications seamlessly.
Why is SSO important?
SSO can increase security in several ways:
-
Reduced password fatigue: With SSO, users must remember and manage only one set of login credentials instead of multiple credentials for different applications. This can reduce the risk of weak or reused passwords, which are more vulnerable to hacking.
-
Centralized access control: SSO allows IT teams to centrally manage and control user access to applications. Access can be granted or revoked from a central identity provider, ensuring that only authorized users have access to sensitive applications.
-
Reduced phishing attacks: Phishing attacks that trick users into giving away their login credentials are common. With SSO, users are less likely to fall for these attacks since they will not be asked to enter their login credentials repeatedly.
-
Multi-factor authentication: SSO can be combined with multi-factor authentication (MFA) to increase security. MFA adds an extra layer of security by requiring users to provide additional authentication factors, such as a fingerprint or a one-time code sent to their mobile device.
-
Audit trails: SSO can provide audit trails that record user access to applications, making it easier to identify and investigate security breaches or unauthorized access attempts.
Overall, SSO can simplify user authentication while increasing security by reducing the risk of weak passwords, centralizing access control, reducing the likelihood of phishing attacks, and enabling MFA and audit trails.
What if an application I’m using doesn’t provide SSO or Multifactor Authentication?
If an application does not provide SSO or MFA, there are still several measures you can take to protect them from cyber threats:
-
Use strong and unique passwords: Encourage users to create strong and unique passwords for each application and avoid reusing passwords across multiple accounts. Passwords should be at least 12 characters long, with a mix of uppercase and lowercase letters, numbers, and symbols.
-
Implement access controls: Use role-based access controls to limit user access to sensitive data and features within the application. Ensure that users are granted access only to the features and data they need to perform their job functions.
-
Regularly update and patch your applications: Keep your applications up-to-date with the latest security patches and software updates. Vulnerabilities in older versions of applications can be exploited by hackers to gain access to your system.
-
Monitor your applications for suspicious activity: Use monitoring tools to detect and respond to any suspicious activity, such as unusual login attempts or access to sensitive data.
-
Train your users: Educate your users on best practices for cybersecurity, such as avoiding phishing emails, not sharing passwords, and being cautious when using public Wi-Fi.
-
Implement multi-factor authentication (MFA) at the user or network level: Even if your applications don’t support MFA, you can still use MFA at the user or network level to provide an extra layer of security. For example, you can use MFA for VPN access or for email access.
While SSO and MFA are effective security measures, they are not the only ways to protect your applications from cyber threats. Implementing strong passwords, access controls, regular updates, monitoring, user training, and MFA can all help improve your application security.